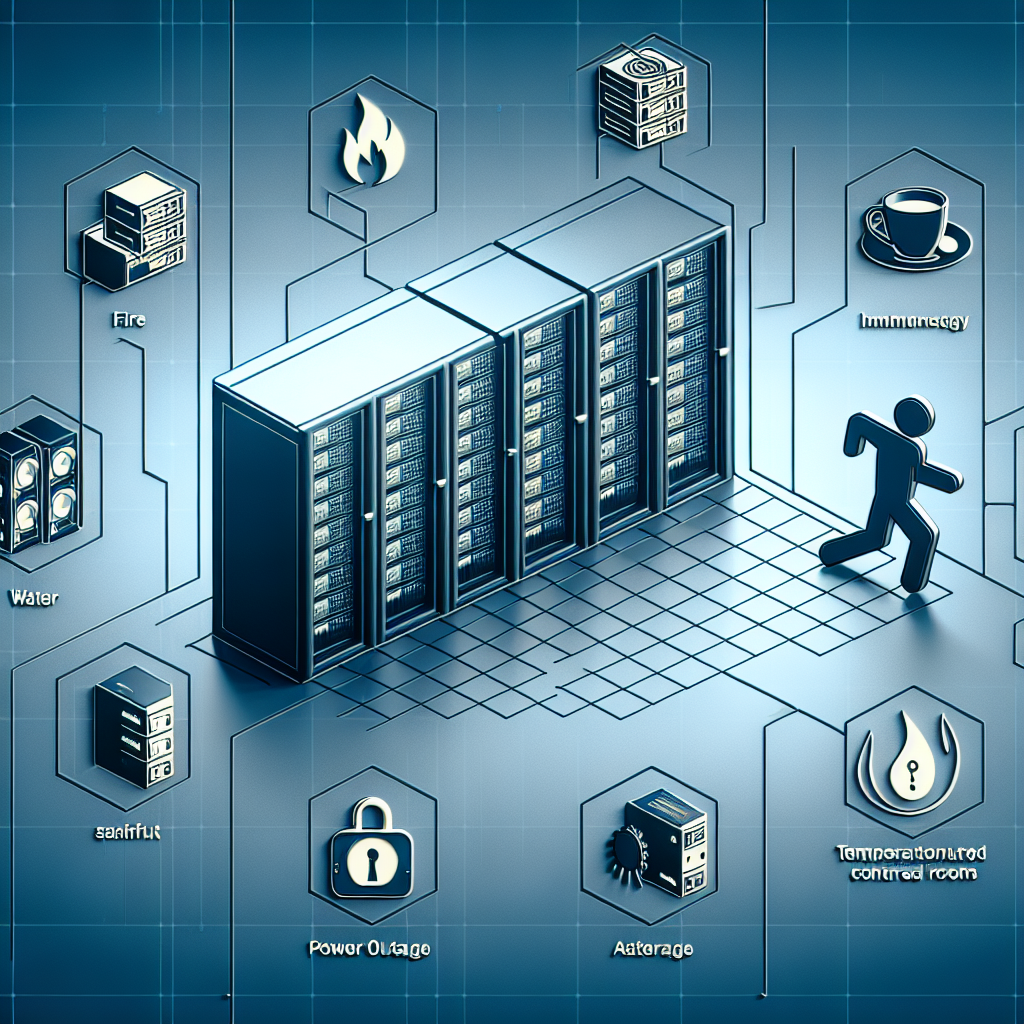
Data centers play a crucial role in storing and managing vast amounts of data for organizations. With the increasing reliance on digital technology, data centers have become prime targets for cyber criminals and other threats. It is essential for organizations to understand the potential risks to their data centers and take proactive measures to mitigate these risks.
One of the first steps in protecting your data center is to conduct a thorough risk assessment. This involves identifying and evaluating potential threats that could compromise the security and integrity of your data. By understanding these threats, organizations can develop a comprehensive strategy to protect their data centers and prevent data breaches.
One of the most common threats to data centers is cyber attacks. Hackers use various techniques such as malware, phishing, and denial of service attacks to gain unauthorized access to sensitive data. These attacks can result in data theft, financial loss, and reputational damage. Organizations must implement robust cybersecurity measures, such as firewalls, encryption, and intrusion detection systems, to prevent cyber attacks and safeguard their data.
Physical threats are another concern for data centers. Natural disasters, such as earthquakes, floods, and fires, can cause significant damage to data center infrastructure and lead to data loss. Organizations should take proactive measures, such as implementing disaster recovery plans, backup systems, and redundant power supplies, to protect their data centers from physical threats.
Human error is also a significant risk to data centers. Employees may unintentionally delete or mishandle data, leading to data loss or corruption. Organizations should provide comprehensive training and strict access controls to minimize the risk of human error and ensure that employees are aware of best practices for data security.
In addition to external threats, organizations must also consider internal threats to their data centers. Insider threats, such as disgruntled employees or contractors, can pose a significant risk to data security. Organizations should implement strict access controls, conduct regular security audits, and monitor employee activities to detect and prevent insider threats.
By conducting a comprehensive risk assessment and understanding the potential threats to their data centers, organizations can develop a proactive and effective strategy to protect their data and minimize the risk of data breaches. Implementing robust cybersecurity measures, disaster recovery plans, and employee training programs can help organizations safeguard their data centers and ensure the security and integrity of their valuable data.