Your cart is currently empty!
Tag: Measures

Proactive Measures for Assessing and Managing Downtime Risk in Data Centers
Data centers are the backbone of modern businesses, providing the infrastructure necessary for storing, processing, and managing large amounts of data. However, downtime in data centers can be catastrophic, leading to lost revenue, damage to reputation, and decreased productivity. That’s why it’s crucial for organizations to take proactive measures to assess and manage downtime risk in their data centers.One of the first steps in assessing and managing downtime risk is conducting a thorough risk assessment. This involves identifying potential sources of downtime, such as power outages, equipment failures, and cyberattacks, and evaluating the likelihood and potential impact of these events. By understanding the risks that their data centers face, organizations can develop strategies to mitigate them and ensure that their data centers remain operational.
One key proactive measure for managing downtime risk is implementing redundancy in critical systems. This involves having backup systems in place for power, cooling, and networking to ensure that data center operations can continue in the event of a failure. Redundancy can help minimize the impact of downtime and ensure that data center services remain available to users.
Regular maintenance and monitoring of data center equipment is also essential for managing downtime risk. By conducting routine inspections, testing, and maintenance, organizations can identify and address potential issues before they lead to downtime. Additionally, monitoring systems can provide real-time data on the performance of data center equipment, allowing organizations to detect and respond to issues quickly.
Another important proactive measure for managing downtime risk is implementing a comprehensive disaster recovery plan. This plan should outline the steps that will be taken in the event of a data center outage, including how data will be backed up, restored, and recovered. By having a well-defined disaster recovery plan in place, organizations can minimize the impact of downtime and ensure that critical data and services are protected.
In addition to these proactive measures, organizations should also regularly test their downtime response procedures to ensure that they are effective and efficient. By conducting regular drills and simulations, organizations can identify any gaps or weaknesses in their response plans and make improvements as needed.
In conclusion, assessing and managing downtime risk in data centers is essential for ensuring the continued operation of critical business services. By taking proactive measures such as conducting risk assessments, implementing redundancy, conducting regular maintenance and monitoring, and implementing a comprehensive disaster recovery plan, organizations can minimize the impact of downtime and protect their data center operations. By being proactive and prepared, organizations can ensure that their data centers remain reliable and resilient in the face of potential disruptions.
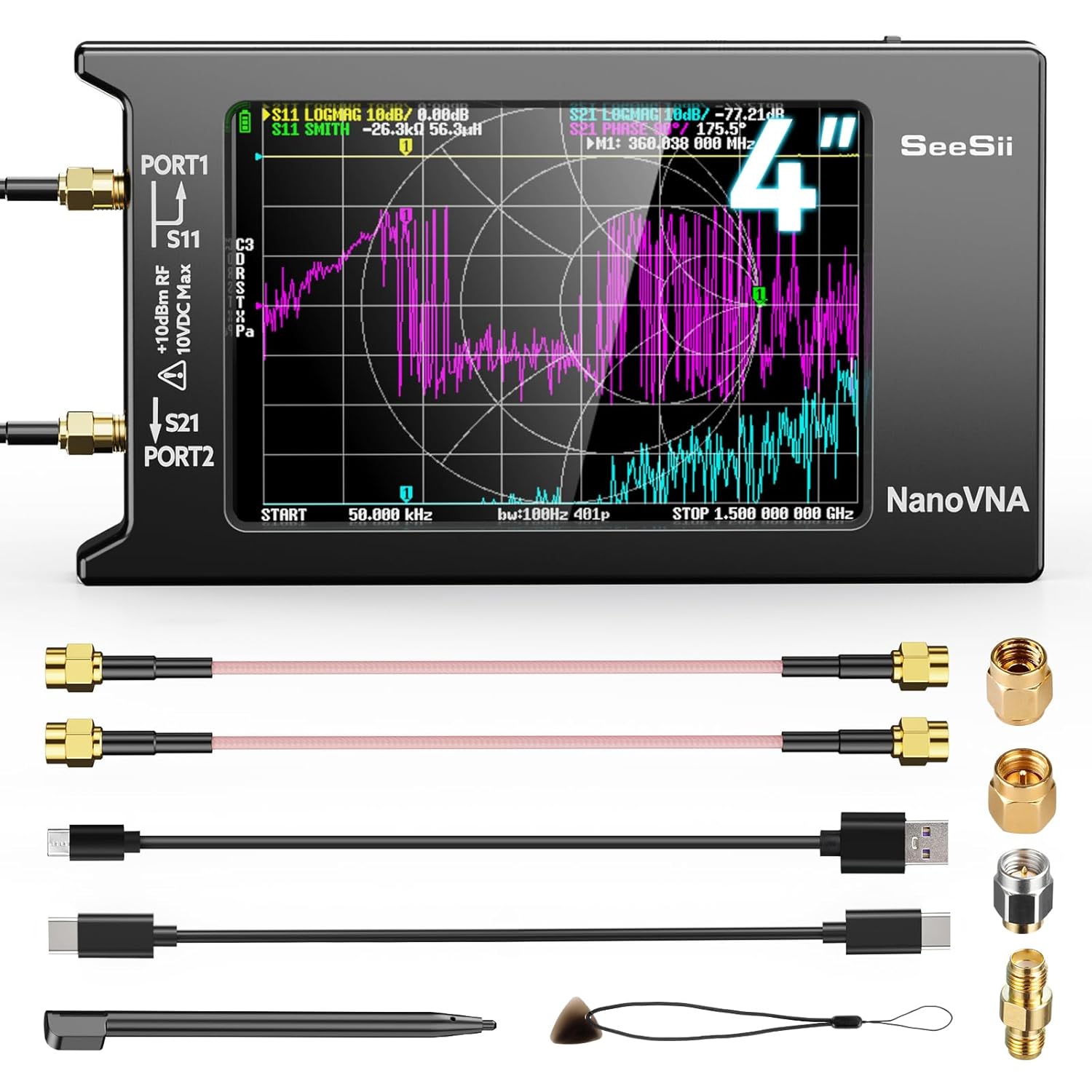
SeeSii Upgraded NanoVNA-H4 Vector Network Analyzer, Latest V4.3 10KHz-1.5GHz HF VHF UHF 4″ Touch Screen VNA Antenna Analyzer Measures S Parameters,Voltage Standing Wave Ratio, Phase,Delay, Smith Chart
Price:$105.99– $98.85
(as of Dec 04,2024 07:17:20 UTC – Details)
Seesii always insists on providing our customers with accurate and practical testing instruments and maintenance equipment.
Package Dimensions : 6.61 x 4.84 x 2.17 inches; 11.99 ounces
Item model number : NanoVNA-H4
Batteries : 1 Lithium Ion batteries required.
Date First Available : March 2, 2020
Manufacturer : Seesii
ASIN : B085CFHTBMUPGRADED NANOVNA ANALYZER: SeeSii Nanovna-h4 Vector Network Analyzer is developed by Hugen. With latest 4.3 version,10KHz-1.5GHz measure range,4.0 inch LCD touchscreen,mini and portable design.This Antenna Analyzer is provides outstanding vector network measurement capabilities and perfect for evaluating antenna resonance and SWR.It is a very handy & smart analyzer for electronics engineer, amateur radio operators or radio diy amateurs
BUILT-IN MICRO-SD PORT & TIME DISPLAY: The lastest antenna analyzer with MicroSD card port,so you can save field test data or screens to a MicroSD card at any time,support up to 32GB memory card. (Not include in the pacakge).In addition, different from old version NanoVNAs, the date and time can be customized, which is convenient for you to further record and save data..The default firmware main function is used for antenna performance measurement
IMPROVED FREQUENCY ALGORITHM:The Vector Network Analyzer can use the old harmonic extension of si5351 to support the measurement frequency up to 1.5GHz. The 50K-300MHz frequency range of the si5351 direct output provides better than 70dB dynamic, The extended 300M-900MHz band provides better than 60dB of dynamics, and the 900M-1.5GHz band is better than 40dB of dynamics.Great for trouble shooting antennas and improving performance
PC CONNECTION & TX/RX FUNCTION:The vna analyzer uses PC software NanoVNASaver, it can connect to a NanoVNA and extracts the data for display on a computer for saving to Touchstone files. We can export Touchstone (snp) files for various radio design and simulation software through PC software.In addition,the default firmware is mainly used for antenna performance measurement. The TX/RX method can measure the complete S11/S21 parameters (need to manually replace the transceiver port wiring)
Abundant Accessories:Equipped with 1x NanoVNA-H4(with 1950mA-h battery), 1x USB Type-C cable, 2 x 15cm SMA male to male RG316 RF cable, 1x SMA male calibration kit – OPEN,1x SMA male calibration kit – SHORT ,1 x SMA male calibration kit – LOAD,1 x Touchscreen pen.It’s very useful as an antenna analyzer for your ham station, easy to set without fancy calibration
Reliable After-Sales Service:We provide professional technical support to keep you away from after-sales worries. If you are not satisfied with SeeSii Nanovna Vector Analyzer or have any other questions, please feel free to contact us. Our after-sales service experts will reply to your information as soon as possible, We will do our best to solve your problems, and you can purchase and experience with confidenceCustomers say
Customers like the functionality, value for money, and accuracy of the product. They mention it’s a very useful tool, works great, and is good quality for the price. Some also like the size. However, some customers have reported issues with the touch screen quality. Opinions differ on ease of use, build quality, and visibility.
AI-generated from the text of customer reviews
Introducing the SeeSii Upgraded NanoVNA-H4 Vector Network Analyzer!Upgrade your testing capabilities with the latest V4.3 version of the NanoVNA-H4, offering a wide frequency range of 10KHz to 1.5GHz for HF, VHF, and UHF applications. This powerful tool comes equipped with a 4″ touch screen display, making it easy to navigate and analyze data.
With the NanoVNA-H4, you can measure S parameters, Voltage Standing Wave Ratio (VSWR), phase, delay, and even generate Smith Charts for a comprehensive understanding of your antenna performance. Whether you’re a hobbyist, engineer, or technician, this VNA antenna analyzer is a must-have for accurate and efficient testing.
Upgrade to the SeeSii Upgraded NanoVNA-H4 Vector Network Analyzer and take your testing capabilities to the next level! #VectorNetworkAnalyzer #AntennaAnalyzer #SeeSii #NanoVNAH4 #UpgradeYourTesting
#SeeSii #Upgraded #NanoVNAH4 #Vector #Network #Analyzer #Latest #V4.3 #10KHz1.5GHz #VHF #UHF #Touch #Screen #VNA #Antenna #Analyzer #Measures #ParametersVoltage #Standing #Wave #Ratio #PhaseDelay #Smith #Chart
Proactive Measures: How to Implement Preventative Data Center Maintenance
Data centers play a crucial role in the operation of modern businesses, housing the critical infrastructure that supports the flow of information and services. As such, it is essential to ensure that these facilities are operating at peak efficiency and reliability. One way to achieve this is through proactive measures, such as preventative data center maintenance.Preventative maintenance involves regularly scheduled inspections, cleaning, and repairs to prevent potential issues before they become major problems. By implementing a preventative maintenance plan, data center managers can reduce the risk of downtime, optimize performance, and extend the lifespan of their equipment.
Here are some key steps to implementing preventative data center maintenance:
1. Develop a maintenance schedule: Start by creating a comprehensive maintenance schedule that outlines the tasks to be performed, the frequency of inspections, and the responsible parties. This schedule should be tailored to the specific needs of your data center and take into account the manufacturer’s recommendations for maintenance.
2. Conduct regular inspections: Regular inspections are essential for identifying potential issues and addressing them before they escalate. Inspect equipment such as servers, cooling systems, power distribution units, and cabling for signs of wear and tear, overheating, or other issues. Keep detailed records of these inspections to track the condition of your equipment over time.
3. Clean and organize: Dust and debris can accumulate in data center equipment, leading to overheating and reduced performance. Regularly clean and organize your data center to ensure optimal airflow and prevent equipment from becoming clogged or obstructed. Use proper cleaning tools and techniques to avoid damaging sensitive equipment.
4. Test backup systems: Data centers rely on backup power systems to maintain operations in the event of a power outage. Regularly test these systems to ensure they are functioning properly and can support the load of your data center. Check batteries, generators, and other backup systems for signs of wear or malfunction.
5. Train staff: Proper training is essential for ensuring that maintenance tasks are performed correctly and safely. Provide training to your data center staff on best practices for maintenance, safety protocols, and emergency procedures. Encourage open communication and collaboration among team members to address issues and share knowledge.
By implementing a preventative maintenance plan, data center managers can proactively address potential issues and minimize the risk of downtime. This approach can help businesses save time and money by avoiding costly repairs and disruptions to operations. With regular inspections, cleaning, and testing, data centers can maintain peak performance and reliability, supporting the needs of modern businesses in an increasingly digital world.

Proactive Measures: How to Implement Preventative Data Center Maintenance
Data centers are the heart of any organization’s IT infrastructure, housing critical systems and data that keep businesses running smoothly. With so much riding on the performance and reliability of these facilities, it’s essential to implement preventative maintenance measures to ensure they operate at peak efficiency.Proactive data center maintenance involves regularly monitoring and maintaining equipment to prevent issues before they occur. By taking a proactive approach, organizations can avoid costly downtime, improve performance, and extend the lifespan of their data center equipment.
Here are some key steps to implementing preventative data center maintenance:
1. Develop a comprehensive maintenance plan: Start by creating a detailed maintenance plan that outlines all the equipment in your data center and the maintenance tasks required for each piece of equipment. This plan should include a schedule for regular inspections, testing, and maintenance tasks.
2. Conduct regular inspections: Regular inspections are essential for identifying potential issues before they escalate into major problems. Inspect all equipment, including servers, cooling systems, UPS units, and networking equipment, for signs of wear and tear, damage, or other issues.
3. Perform routine maintenance tasks: In addition to inspections, regular maintenance tasks such as cleaning, testing, and lubricating equipment should be performed according to the manufacturer’s guidelines. This can help prevent equipment failures and ensure optimal performance.
4. Monitor environmental conditions: Data center equipment is sensitive to environmental conditions such as temperature and humidity. Monitoring these conditions and taking corrective action when necessary can help prevent equipment failures and ensure optimal performance.
5. Implement remote monitoring and management tools: Remote monitoring and management tools can help data center staff monitor equipment performance, detect issues in real-time, and take corrective action before they impact operations. These tools can also help automate routine maintenance tasks and streamline maintenance processes.
6. Train staff: Proper training is essential for ensuring that data center staff are equipped to perform maintenance tasks effectively and safely. Training should cover equipment operation, maintenance procedures, safety protocols, and troubleshooting techniques.
7. Document maintenance activities: Keep detailed records of all maintenance activities, including inspections, tests, repairs, and replacements. This documentation can help track equipment performance, identify recurring issues, and plan future maintenance tasks.
By implementing proactive maintenance measures, organizations can minimize downtime, improve equipment reliability, and optimize data center performance. With a comprehensive maintenance plan, regular inspections, routine maintenance tasks, environmental monitoring, remote monitoring tools, staff training, and documentation, organizations can ensure that their data centers operate at peak efficiency and remain resilient in the face of potential issues.

Enhancing Security Measures: Updates on Cybersecurity Programs and Policies in the 3rd Edition
In today’s digital age, cybersecurity has become more important than ever before. With the increasing number of cyber threats and attacks targeting businesses, governments, and individuals, it is crucial to stay updated on the latest cybersecurity programs and policies to enhance security measures and protect sensitive data.The third edition of cybersecurity programs and policies focuses on enhancing security measures to address the evolving cyber threats landscape. This edition includes updates on new technologies, best practices, and regulations to combat cyber attacks effectively.
One of the key updates in the third edition is the introduction of advanced threat detection technologies such as artificial intelligence and machine learning. These technologies can help organizations detect and respond to cyber threats in real-time, preventing potential data breaches and attacks.
Another update in the third edition is the emphasis on employee training and awareness programs. Human error is still one of the leading causes of data breaches, so it is essential for organizations to educate their employees on cybersecurity best practices and how to identify and report potential threats.
Additionally, the third edition includes updates on compliance regulations and data protection laws. With the increasing number of data privacy regulations such as GDPR and CCPA, organizations need to ensure they are compliant with these laws to avoid hefty fines and reputational damage.
Furthermore, the third edition of cybersecurity programs and policies also addresses the importance of implementing a robust incident response plan. In the event of a cyber attack, organizations need to have a well-defined plan in place to contain the breach, minimize the damage, and recover quickly.
Overall, the third edition of cybersecurity programs and policies provides valuable insights and updates on how organizations can enhance their security measures to protect against cyber threats effectively. By staying informed and implementing the latest technologies and best practices, organizations can safeguard their sensitive data and mitigate the risks associated with cyber attacks.

Ensuring Business Continuity Through Robust Data Center Fire Suppression Measures
In today’s digital age, data centers play a crucial role in keeping businesses operational and functioning smoothly. These facilities house servers, storage devices, and networking equipment that are essential for storing and processing data. However, one of the biggest threats to data centers is fire. A fire in a data center can lead to catastrophic loss of data, downtime, and financial repercussions for businesses. That is why it is essential for businesses to have robust fire suppression measures in place to ensure business continuity.There are several fire suppression systems that can be implemented in data centers to protect equipment and data in the event of a fire. One of the most common systems is a water-based sprinkler system. These systems are effective at extinguishing fires, but they can also cause significant water damage to equipment and data. As a result, many data centers opt for more advanced fire suppression systems, such as clean agent systems.
Clean agent fire suppression systems use chemicals that are safe for electronic equipment and will not leave a residue after discharge. These systems work by releasing a gas that extinguishes the fire by removing oxygen from the environment. This type of system is ideal for data centers because it can quickly suppress a fire without causing damage to equipment or data.
Another important aspect of ensuring business continuity through robust data center fire suppression measures is regular testing and maintenance of the system. It is crucial to conduct regular inspections, testing, and maintenance of the fire suppression system to ensure that it is functioning properly and will effectively suppress a fire when needed. This includes checking for leaks, ensuring that all components are in working order, and replacing any faulty equipment.
In addition to having a reliable fire suppression system in place, data centers should also have a comprehensive fire prevention plan. This includes implementing fire detection systems, such as smoke detectors and heat sensors, to alert staff of a potential fire before it escalates. It is also essential to have proper fire safety training for employees so that they know how to respond in the event of a fire.
Overall, ensuring business continuity through robust data center fire suppression measures is essential for protecting equipment, data, and the overall operations of a business. By implementing advanced fire suppression systems, conducting regular maintenance, and having a comprehensive fire prevention plan in place, businesses can minimize the risk of a catastrophic fire and ensure that their data center remains operational in the face of a fire emergency.

Creating a Secure Data Center Environment: Tips for Enhancing Safety Measures
In today’s digital age, data centers play a crucial role in storing and managing vast amounts of critical information for businesses and organizations. With cyber threats on the rise, it is more important than ever to ensure that your data center is secure and protected from potential breaches and attacks. Here are some tips for enhancing safety measures and creating a secure data center environment.1. Implement Access Control Measures:
One of the first steps in enhancing data center security is to implement access control measures. This includes using keycards, biometric scanners, and security guards to restrict access to only authorized personnel. By limiting who can enter the data center, you can reduce the risk of unauthorized access and potential security breaches.
2. Monitor and Audit Access:
In addition to restricting access, it is important to monitor and audit all access to the data center. This includes keeping track of who enters and exits the facility, as well as monitoring any changes made to the data center’s infrastructure. By maintaining a record of access and activities, you can quickly identify and respond to any suspicious behavior.
3. Secure Physical Infrastructure:
Physical security is just as important as cybersecurity when it comes to protecting your data center. Make sure that the facility is equipped with security cameras, alarm systems, and other physical security measures to deter unauthorized access. Additionally, consider implementing measures such as secure cages and enclosures to protect servers and other critical equipment from theft or damage.
4. Implement Data Encryption:
Data encryption is a crucial security measure for protecting sensitive information stored in your data center. Encrypting data ensures that even if it is accessed by unauthorized parties, it cannot be read or understood without the proper decryption key. Make sure to implement strong encryption protocols for all data stored in your data center to keep it secure from potential breaches.
5. Regularly Update Security Protocols:
Cyber threats are constantly evolving, so it is important to regularly update your security protocols to stay ahead of potential risks. This includes patching software vulnerabilities, updating firewall rules, and conducting regular security audits to identify and address any weaknesses in your data center’s security infrastructure.
6. Train Staff on Security Best Practices:
Your employees play a crucial role in maintaining data center security, so make sure to provide them with training on security best practices. This includes educating them on how to recognize and respond to potential security threats, as well as implementing strong password policies and other security measures to protect sensitive information.
By following these tips for enhancing safety measures in your data center, you can create a secure environment that protects your critical information from potential breaches and attacks. Remember that data security is an ongoing process, so make sure to regularly review and update your security measures to stay ahead of potential threats.

How IT Solutions Can Enhance Cybersecurity Measures
In today’s digital age, cybersecurity has become a top priority for businesses of all sizes. With the increasing number of cyber threats and attacks, it is essential for companies to invest in robust cybersecurity measures to protect their data and systems. One way to enhance cybersecurity measures is by implementing IT solutions that can help prevent, detect, and respond to cyber threats effectively.IT solutions play a crucial role in enhancing cybersecurity measures by providing businesses with the tools and technologies needed to secure their networks, systems, and data. These solutions help businesses identify vulnerabilities, monitor network activity, and respond to security incidents in a timely manner. By leveraging IT solutions, businesses can strengthen their cybersecurity posture and prevent potential breaches or attacks.
One of the key benefits of IT solutions in enhancing cybersecurity measures is their ability to provide real-time visibility into network activity. By monitoring network traffic and analyzing data in real-time, businesses can detect any unusual or suspicious behavior that may indicate a potential cyber threat. This proactive approach to cybersecurity allows businesses to respond quickly to security incidents and mitigate any potential damage before it escalates.
Additionally, IT solutions can help businesses automate security processes and streamline incident response procedures. By implementing security automation tools, businesses can reduce the time and resources required to respond to security incidents, allowing them to address threats more efficiently and effectively. This automation also helps businesses improve their overall cybersecurity posture by ensuring consistent and timely responses to security incidents.
Furthermore, IT solutions can help businesses enforce security policies and compliance requirements to protect their data and systems. By implementing access controls, encryption, and other security measures, businesses can ensure that only authorized users have access to sensitive information and systems. This helps businesses prevent data breaches and comply with industry regulations and standards, such as GDPR or HIPAA.
Overall, IT solutions play a vital role in enhancing cybersecurity measures by providing businesses with the tools and technologies needed to protect their data and systems from cyber threats. By investing in IT solutions, businesses can strengthen their cybersecurity posture, detect and respond to security incidents in a timely manner, and ensure compliance with industry regulations and standards. In today’s digital landscape, IT solutions are essential for businesses looking to safeguard their data and systems from cyber threats.

Protecting Your Company from Inc Hacking: Top Security Measures to Implement
In today’s digital age, cybersecurity is more important than ever. With the rise of hacking incidents targeting companies and organizations, it’s crucial for businesses to take proactive steps to protect themselves from potential breaches. One of the most common forms of cyber attacks is Inc Hacking, where hackers target a company’s internal systems and confidential information.To safeguard your company from Inc Hacking, it’s essential to implement top security measures. Here are some key steps you can take to enhance your cybersecurity:
1. Employee Training: One of the most common ways hackers gain access to a company’s systems is through phishing emails. Educate your employees on how to identify and avoid suspicious emails, links, and attachments. Regular training sessions can help reinforce the importance of cybersecurity practices.
2. Strong Password Policies: Ensure that your employees use strong, unique passwords for all their accounts and devices. Implement multi-factor authentication for an added layer of security. Regularly update passwords and encourage employees to use password managers to securely store their credentials.
3. Secure Network Infrastructure: Secure your company’s network with firewalls, encryption, and intrusion detection systems. Regularly monitor network traffic for any signs of suspicious activity. Implement secure Wi-Fi networks and restrict access to sensitive information.
4. Regular Software Updates: Keep all software and operating systems up to date with the latest security patches. Regularly update antivirus and anti-malware programs to protect against known threats. Consider using automated patch management tools to ensure timely updates.
5. Data Encryption: Encrypt sensitive data both at rest and in transit. Use encryption protocols such as SSL/TLS for secure communication over the internet. Implement encryption for email communications and file storage to protect confidential information from unauthorized access.
6. Secure Remote Access: If employees work remotely or access company systems from outside the office, ensure that remote access is secure. Use virtual private networks (VPNs) and secure remote desktop protocols to encrypt communication and authenticate users.
7. Incident Response Plan: Develop a comprehensive incident response plan to quickly respond to security breaches. Establish clear protocols for reporting incidents, containing threats, and restoring systems. Regularly test and update the plan to address evolving threats.
By implementing these top security measures, you can better protect your company from Inc Hacking and other cyber threats. Stay vigilant, stay informed, and prioritize cybersecurity to safeguard your business and its valuable assets. Remember, investing in cybersecurity now can save you from costly data breaches and reputational damage in the future.

Preparing for the Unexpected: Implementing Business Continuity Measures
In today’s fast-paced business world, it is crucial for companies to be prepared for the unexpected. Whether it’s a natural disaster, a cyber attack, or a global pandemic, businesses need to have plans in place to ensure they can continue operating and serving their customers even in the face of adversity. This is where business continuity measures come into play.Business continuity is the process of creating a plan to ensure that essential business functions can continue in the event of a disruption. This can include everything from having backup power sources in case of a blackout, to setting up remote work capabilities for employees in case of a pandemic. By implementing business continuity measures, companies can minimize the impact of unexpected events and ensure that they can continue to operate smoothly.
One key aspect of preparing for the unexpected is conducting a risk assessment. This involves identifying potential threats to your business, such as natural disasters, cyber attacks, or supply chain disruptions. By understanding the risks your business faces, you can develop a plan to mitigate them and ensure your business can continue operating in the face of adversity.
Another important step in implementing business continuity measures is creating a business continuity plan. This plan should outline how your business will respond to various scenarios, such as a cyber attack or a natural disaster. It should include details on how essential functions will be maintained, how communication will be managed, and how employees will be kept safe. By having a detailed plan in place, your business can respond quickly and effectively to unexpected events.
In addition to creating a business continuity plan, companies should also test their plans regularly. This can involve running simulations of various scenarios to ensure that employees understand their roles and responsibilities, and that systems are functioning properly. By testing your plans regularly, you can identify any weaknesses and make necessary adjustments to ensure your business is prepared for the unexpected.
Finally, it is important for companies to regularly review and update their business continuity measures. As technology and threats evolve, so too should your business continuity plan. By staying informed about potential risks and continuously improving your plan, you can ensure that your business is prepared for whatever challenges may come its way.
In conclusion, preparing for the unexpected is crucial for businesses of all sizes. By implementing business continuity measures, companies can minimize the impact of unexpected events and ensure they can continue operating smoothly. By conducting risk assessments, creating a detailed business continuity plan, testing their plans regularly, and staying informed about potential risks, businesses can ensure they are prepared for whatever challenges may come their way.
